Most antivirus programs–or “security suites”, as they call themselves–want you to install their browser extensions. They promise these toolbars will help keep you safe online, but they usually just exist to make the company some money. Worse yet, these extensions are often hideously vulnerable to attack.
Many antivirus toolbars are, at best, just rebranded Ask Toolbar extensions. They add a toolbar, change your search engine, and give you a new homepage. They may brand it as a “secure” search engine, but it’s really just about making the antivirus company money. But in some cases, they do more than that–and sometimes with unintended consequences.
Example 1: AVG Web TuneUP Broke Chrome’s Security
“AVG Web TuneUP” is installed when you install AVG antivirus. According to the Chrome Web Store, it has nearly 10 million users. AVG’s official description of the extension says it will “warn you of unsafe search results.”
Back in December, Google-employed security researcher Tavis Ormandy discovered that the extension adds a large number of new JavaScript APIs to Chrome when it’s installed and that “many of the APIs are broken.” Aside from exposing your entire browsing history to any website you visit, the extension offered many security holes for websites to easily execute arbitrary code on any computer with the extension installed.
“My concern is that your security software is disabling web security for 9 million Chrome users, apparently so that you can hijack search settings and the new tab page,” he wrote to AVG. “I hope the severity of this issue is clear to you, fixing it should be your highest priority.”
Four days after it was reported, AVG had a patch. As Ormandy wrote: “AVG submitted an extension with a “fix”, but the fix was obviously incorrect.” He had to provide instructions for how to fix this flaw, and AVG issued an updated patch a day later. The fix restricts the functions to two specific AVG domains, but, as Ormandy noted, the websites on those domains have their own flaws that opens users up to attack.
Not only did AVG ship a browser extension with obviously broken, shoddy, insecure code, but AVG’s developers couldn’t even fix the problem without having their hands held by a Google security researcher. Hopefully, the browser extensions are being developed by a different team and the real experts are working on the antivirus software itself–but that’s a good example of how those antivirus browser extensions can go from useless to harmful.
Example 2: McAfee and Norton Don’t Think Microsoft Edge Is Secure (Because It Doesn’t Support Their Add-On)
mcafee-webadvisor-edge-protection-warning
If you’ve been following the development of Microsoft Edge for Windows 10, you’ll know that it’s supposed to be a more secure web browser than Internet Explorer. It runs in a sandbox and abandons support for old, insecure plug-in technologies like ActiveX. It has a more streamlined codebase and a variety of other improvements, such as protection against “binary injection,” where other programs inject code into the Microsoft Edge process.
And yet, McAfee–which is even installed by default on many new Windows 10 PCs–really doesn’t want you to use Microsoft Edge. Instead, McAfee recommends you use Internet Explorer, and will helpfully remove Edge from your taskbar and pin Internet Explorer there if you let it. All so you can keep using the McAfee browser extension.
Even if that browser extension helped keep you secure a little bit–something we don’t really believe–you’d be much better off with the improved security in Microsoft Edge. Norton does something similar, recommending you use a “supported browser” like Internet Explorer on Windows 10.
Thankfully, Microsoft Edge will soon support Chrome-style browser extensions. And when it does, McAfee and Norton can force their browser extensions on Edge users and stop redirecting them to the old-and-out-of-date-IE.
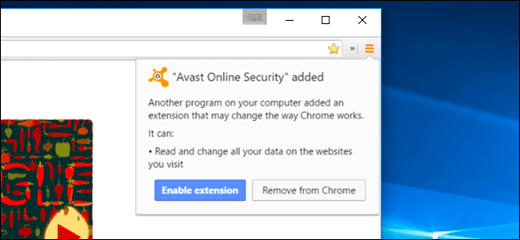
Example 3: Avast’s Online Security Extension Once Included Ads and Tracking
Here’s one we’ve covered before: Avast installs an “Avast! Online Security” browser extension when you install the main security suite, and they later added a feature named “SafePrice” to the extension in an update. This feature was enabled by default, and it displayed online shopping recommendations–in other words, ads that presumably make Avast money when you click them–as you browse.
To do this, it assigned you a unique tracking ID and sent every single web page you visited to Avast’s servers, associated with that unique ID. In other words, Avast tracked all your web browsing and used it to show ads. Thankfully, Avast eventually removed SafePrice from its main browser extension. But antivirus companies clearly see their “security” extensions as an opportunity to dig deep into the browser and show you ads (or “product recommendations”), not just a way to keep you secure.
It’s Not Just Browser Extensions: You Should Disable Other Browser Integrations, Too
Extensions are just part of the problem. Any form of browser integration can create security holes. Antivirus programs often want to monitor all your network traffic and inspect it, but they can’t normally see what’s happening inside an encrypted connection, like the one you use to access your email, or bank, or Facebook. After all, that’s the point of encryption–to keep that traffic private. To get around this limitation, some antivirus programs effectively perform a “man-in-the-middle” attack so they can monitor what’s actually going on over an encrypted connection. These work an awful lot like Superfish, replacing certificates with the antivirus’s own. The MalwareBytes blog explained avast!’s behavior here.
This feature is generally just an option in the antivirus program itself, and not part of a browser extension, but it’s worth discussing all the same. For example, Avast’s SSL-interception code contained an easily exploitable security hole that could be used by a malicious server. “At least get an intern to skim your before shipping it,” tweeted Ormandy after discovering the problem. It’s one of those bugs that Avast, a security company, should have caught before shipping it to users.
As he argued in following tweets, this sort of man-in-the-middle code just adds more “attack surface” to the browser, giving malicious sites another way to attack you. Even if the developers of your security program are more careful, features that tamper with your browser are a lot of risk for not much reward. Your browser already contains anti-malware and anti-phishing features, and search engines like Google and Bing already attempt to identify dangerous websites and avoid sending you there.
You Don’t Need These Features, So Disable Them
img_56a2c8a932c54
Here’s the thing: even barring the above issues, these browser extensions are still unnecessary.
Most of these antivirus products promise to make you more secure online by blocking bad websites, and identifying bad search results. But search engines like Google already do this by default, and phishing and malware page filters are built into Google Chrome, Mozilla Firefox, and Microsoft’s web browsers. Your browser can handle itself.
So whatever antivirus program you use, don’t install the browser extension. If you already installed it or weren’t given a choice (many install their extensions by default), visit the Extensions, Add-ons, or Plug-ins page in your web browser and disable any extensions associated with your security suite. If your antivirus program has some sort of “browser integration” that breaks the way basic SSL encryption is supposed to work, you should probably disable that feature too.
Interestingly enough, Ormandy–who’s found a variety of security holes in many, many different antivirus programs–ends up recommending Microsoft’s Windows Defender, stating that it’s “not a complete mess” and “has a reasonably competent security team.” While Windows Defender certainly has its flaws, at least it doesn’t attempt to insert itself into the browser with these additional features.
Of course, if you want to use a more powerful antivirus program than Windows Defender, you don’t need its browser features to stay secure. So if you download another free antivirus program, be sure to disable its browser features and extensions. Your antivirus can keep you safe from malicious files you might download and attacks on your web browser without those integrations.